Platform Security. A simple phrase, but one which kicks off a flood of questions for you and I, the user of a Symbian OS 9-based device. In this feature, I'll try and answer them all.
"I'm afraid of contracting a virus - I thought Symbian OS 9's 'Platform Security' was supposed to make viruses impossible?"
As I've often said (link), true viruses/trojans (malicious software, or 'malware') are impossible on any version of Symbian OS because they can't install themselves invisibly. Having said that, users can still opt to install (through multiple confirmations) any application, even if they knowingly got it from a 'warez' site, i.e. they choose to take a risk.
What's different on Symbian OS 9 devices (currently S60 3rd Edition or UIQ 3) is that the critical 'capabilities' of the OS are hidden away unless an application is 'Symbian Signed' (i.e. checked independently and fully traceable to its creator). So even if a user presses ahead and chooses to install something from the warez/malware world, the OS itself won't let the application do anything that might cause it to propagate over the phone network or Internet. Bluetooth transmission is still possible, with specific user permission, but the spread of such a malicious piece of software is going to be very limited.
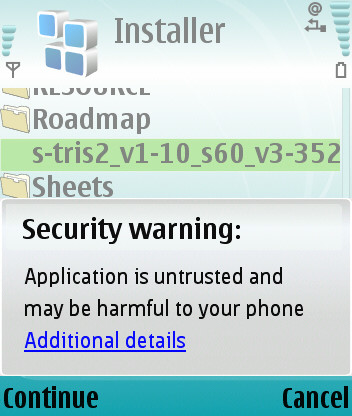
"So what's the point in Nokia including the install package for an anti-virus utility in many of their smartphones?"
Good question. There's not really any point as there isn't any S60 3rd Edition (or UIQ 3) malware in the wild, for the reason mentioned above. There are still 'bad' things a trojan might do to your smartphone, including deleting public files or messing with your PIM data, but restoring these files is normally trivial (e.g. by sync/overwriting from PC). There's also the very remote possibility of vulnerabilities being discovered in existing built-in or 3rd party signed applications, whereby an unsigned app could hook into their allowed functionality, and I suppose a security utility might provide temporary detection and relief, but this is clutching at straws. Simply staying away from cracked/warez applications and only downloading from trusted web sites is all you need to do to avoid such malware.
The main reason, however, that Nokia supply a security utility (in uninstalled form, tellingly) is I suspect for public relations, to be seen to be responding to media scare stories.
"Say I do download an 'untrusted' application (it pops up the 'Application is untrusted and may be harmful to your phone' message when you install it). What can it and what can't it do?"
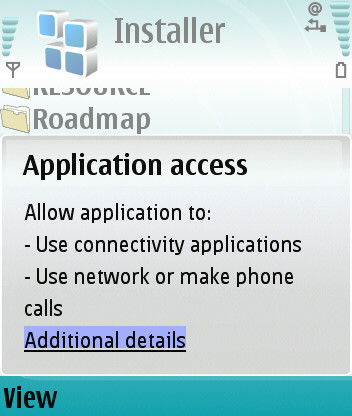
Quite a bit, although you'll be warned, at install time, about any OS capabilities it's going to ask for. For example, access to the Web, access to Bluetooth or infrared, plus the ability to read/write to your PIM (Calendar, Contacts, etc.) data. Note that it won't be able to touch system files or data in other applications or (most importantly) send a SMS or MMS without explicit user permission at run time (the most usual methods for potential malware to propagate).
"Some applications I install don't ask for any confirmation of these capabilities. What does this mean?"
Either such an application is relatively trivial (such as games) and so doesn't need access to any advanced functions, or it's been officially 'Symbian Signed', meaning that an independent company has checked it out and approved it as allowing to use the capabilities mentioned above plus many more that are more 'restricted'. Either way, you don't need to worry.
"What's 'self-signing'?"
This is how applications get created when they're not put through the independent Symbian Signing process, which is overly expensive for some developers to get involved with. Yet all programs have to be signed for Symbian OS to accept them (i.e. so that each is traceable and so that it knows they haven't been tampered with). With self-signing, essentially, the developer signs the application with their own details. As mentioned above, this is quite feasible if the program doesn't need any advanced capabilities.
In other words, in order for a S60 3rd Edition (or UIQ 3) piece of malware to be installed at all, it would need to be self-signed by the programmer. This basically means encoding some contact details into the signed installation file - though in the case of malware these would (unless the programmer was very stupid) be made up or fraudulently using someone else's details. Either way, you'd probably be suspicious.
The future (Steve's soapbox!)
As many observers have noted, most users simply click 'Yes' or 'Continue' to any dialogs brought up during installation, which makes a bit of a mockery of the warnings themselves. But, as explained above, even after choosing to press through and unstall a self-signed 'untrusted' application, it's limited in the degree to which it can damage your smartphone and it's very limited in terms of it doing something malicious to other smartphone owners. Nevertheless, Nokia has chosen to default all Eseries devices to only installing proper Symbian Signed applications (though the setting can be turned off if the user feels that they know what they're doing). And it's possible that some future devices from Symbian OS licensees may come hard coded to only install Symbian Signed applications.
The popular media would have us believe that malware is rampant among smartphone users (mainly on the back of irresponsible press releases by security firms) and you can't blame manufacturers and networks from running a little scared. But in the real world there are (literally) millions of smartphone owners enjoying their devices to the full, many of whom also happily install applications from trustworthy stores/download sites.
It shouldn't be left to the (tiny) malware and (sadly growing) warez scenes to dictate how the majority of owners use their smartphones.
Symbian OS's Platform Security is, in my opinion, a necessary and sufficient step to keep the smartphone world under control. And now you know (nearly) as much about it as I do!
Steve Litchfield, November 2006
