Review: Track and Protect 2
Rafe reviews the updated version 2 of Klomptek's Track and Protect, which he describes as the 'Rolls Royce' of remote security, allowing not only the traditional locking and wiping functions but also super-cool recovery actions like getting the phone to report its own whereabouts to you over the web (even if the finder/thief puts in a new SIM) and taking photos of anyone trying to 'break in'. Read on for a full breakdown of Track and Protect's capabilities.
Version Reviewed: 2
Buy Link | Download / Information Link
Introduction
How valuable is your mobile phone to you? The answer is going to be different for everyone, but I suspect a common element is that the value of the phone extends significantly beyond its actual financial value. That's because mobile phones are devices that have a strong personal connection for many people. But more than anything else, there's value in the content that is stored in the mobile phone, as we have previously discussed:
Then there's the content, it's not just about contacts any more, there are text messages, emails, photos, music, applications and more too. Chances are your phone has stored log-ins for your social networking accounts, giving easy access to Twitter, Facebook and more. It's no surprise then that an ever increasing number of people say that their mobile is one of their most important possessions.
Losing your phone, which will probably happen to almost everyone sooner or later, be it through theft or accident, can be a traumatic experience. Financial value and content aside there's also the inconvenience on having to arrange a replacement, and a strong sense of being disconnected.
The corporate world has long worried about the security of sensitive data on mobile devices and consequently there are many solutions that focus on securing data or allowing the device to be controlled from afar (remote management). These usually revolve around locking a device, so its data can not be accessed, or wiping the data altogether. Some of these enterprise solutions are available to consumers (e.g. the built in SMS lock facility in Nokia's Eseries devices), but the emphasis tends to be on data protection rather enabling the retrieval of the phone.
In the last few years, consumer-focussed remote management solutions have started to appear, such as WaveSecure and Apple's 'Find My iPhone' service. But the true Rolls Royce of this market has to be Klomptek's Track and Protect. When we last looked at Track and Protect, late last year, it was still in beta; since then it has had its formal release and gone through several iterations, adding extra stability and functionality.
Set-up and security
Track and Protect has two key areas of functionality, firstly as a security application for your phone (passcode protection) and secondly as a remote management tool (control and track the phone remotely). It consists of an application that you install on your phone (handling security and enabling remote management) and a web service (allowing you to control the phone remotely).
When you first install Track and Protect, you are walked through a simple set up procedure. You'll be asked to provide various pieces of information, including your phone number, email address and a security PIN. After this has been entered, the application contacts the Track and Protect server and sets up an account for you. With the service activated, you are invited to visit the Track and Protect web site where you can log into your account and start using the service. It's clear that the developers have strived to make the whole process as painless as possible.
The basic security feature of Track and Protect is the lock screen at which you must enter your security PIN to continue using the phone. There are a number of optional settings, including controlling when you want the phone to be locked (i.e. times at which you'll have to enter your security PIN). These include 'lock at switch on', 'lock in offline' (you want the phone online so remote commands can get though), 'passcode check' (locks once, twice, or three times a day), and 'block uninstall' (locks when you access App. manager). Whether you choose to enable or disable these locks is entirely up to you, but I would recommend keeping the 'lock in offline' and 'block uninstall' as a minimum, as they are necessary to maintain full security in the time between losing the phone and activating a remote lock.
The protection level provided by Track and Protect is excellent, changing the SIM card will have no effect (indeed it will be reported to the web site), nor can the application be uninstalled (install/uninstalls are protected), even a standard phone firmware flash will have no impact (you would need the passcode to proceed). This basic level of security, depending on the options enabled, is probably sufficient to provide an acceptable level of security for most people. But it is the remote management features that offer the real power and even the opportunity to retrieve a lost or stolen device.
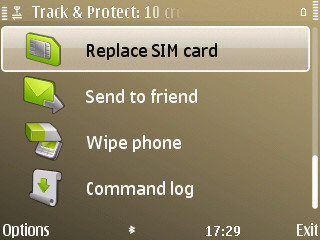
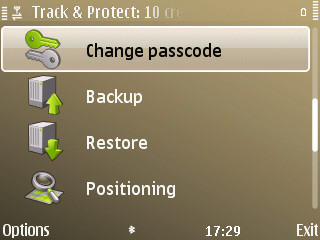
Remote management
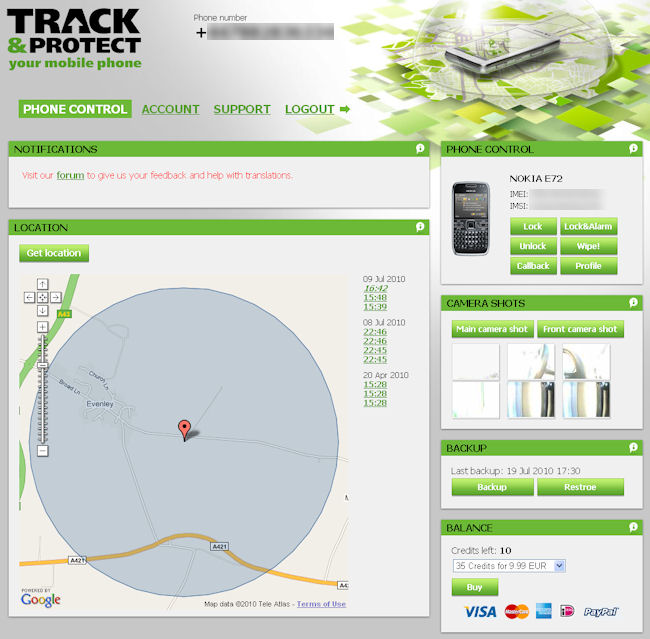
The remote management features of Track and Protect allow remote commands to be sent to the phone. To send commands and see the responses to them you log-in to the Track and Protect website. This provides an easy to use control panel for the various commands. The commands are sent as 'silent' text messages. The phone receives the text message, but it is intercepted by Track and Protect, and thus there's no sound, no notification of a tell-tale text message sitting in your inbox. Within a few seconds the Track and Protect application implements the appropriate command.
Here's a run through of the available commands:
- Lock - locks the phone and displays the 'remote lock' screen. This is slightly different from the normal lock screen. It displays owner and reward information, which encourages whoever finds the phone to return it to you. It also allows for calls to be made, but only to three preset numbers (home phone, work phone, friend's phone). This means that if someone finds the phone then they can still call you to arrange to return the phone, but they cannot use it for anything else. The owner information, reward and pre-set numbers can all be configured in the application settings.
- Lock and Alarm - is the same as Lock, but additionally sounds an alarm. It might just be enough to cause a thief to throw the phone away. It's also handy for locating a phone lost under a pile of papers.
- Unlock - unlocks the phone.
- Wipe - wipes the contents of both the phone's memory and the memory card (the second of which is often missed by similar solutions).
- Callback - instructs the phone to call the specified number. This means you can listen to wherever the phone is. It's obviously a significant improvement over ringing the phone and hoping someone will answer.
- Profile - changes to the specified profile; this is particularly useful if your phone is in silent mode and you want to be able to hear it when it rings.
- Get Location - send the phone's current location to the Track and Protect server. The location will be displayed on a map. Track and Protect will send as precise a location as possible, first using GPS and then, if the GPS does not work, using cell tower location.
- Camera Shots - captures an image from either the front or rear cameras and then sends it to the Track and Protect server. This can be used to help identify where the phone is (if lost) or, if you're lucky, capture a picture of the thief (if stolen).
Each of these commands costs one credit. Credits can be bought, on a pay as you go basis, from the Track and Protect web site (by card or PayPal). At the time of writing, the credits cost 5 Euro for 15 credits, 10 Euro for 35 credits and 15 Euro for 55 credits. Even at its most expensive, that's a cost of just 33 Euro-cents per command, which is extremely good value.
The Track and Protect software itself is free. This means that you don't need to pay anything until you need to send remote commands. However I would suggest buying at least 5 Euros worth of credits so you can see how the system works and so you're ready to go should the worse happen.

Also worth a mention here is Track and Protect's ability to let you swap SIMs, either permanently or temporarily. This means you can use a different SIM card when you are abroad to take advantage of cheaper calling and data rates, and still maintain the protection of Track and Protect. It also means the pre-bought credits remain valid regardless of how many times you change your SIM card or device.
Extra functionality and features
Track and Protect also has some additional features, the most notable of which is the backup and restore system. These can be activated from either the application on the phone or as a remote command. The backup functionality will copy your contacts, calendar and note entries from your phone and store them securely on the Track and Protect website. The restore function will copy them back to your phone. It's a logical feature to include and gives added peace of mind. Unfortunately, by definition, if you do have to use it, it is either because the original phone is broken or you were unable to retrieve the phone after it was lost or stolen.
Given that the remote commands work via SMS, one of the issues to look out for, with applications like Track and Protect, is what happens when a different SIM card is inserted (also known as an 'alien SIM' ). Track and Protect handles this issue admirably, it recognises when a new SIM card has been inserted and notifies the server so that subsequent commands can be sent to the new number. It will also show the new number and the operator on the web site, which can be valuable information to pass on to the police.
A similar automatic information collection occurs if Track and Protect's passcode is entered incorrectly three times. A picture is captured from the front and camera and uploaded to the Track and Protect server. And, of course, this is precisely the moment someone is most likely to be looking at the front camera, which means you have a good chance of catching someone in the act.
So does it really work?
The key test of an application is whether it works in the real world. I've used Track and Protect a number of times to help locate my phone when I've left it under a pile of papers or it rolled down the back of the sofa, but on a recent day out I had inadvertently had an opportunity to really put it to the test.
While attending a practice day of the British Grand Prix I manged to mislay my E72. I wasn't sure whether I had lost it or someone had stolen it. Fortunately I had a laptop with me so was able to fire up the Track and Protect website and send an immediate lock command to the phone. I then tried sending a 'Get Location' command, but didn't get any response initially (as it would later turn out, the phone was under a metal seat and couldn't get a GPS fix). However, after about ten minutes a rough (cell tower-based) location did arrive, but it didn't really help since it indicated an area several miles in diameter.
Feeling rather annoyed, I resigned myself to a lost phone, at least for the time being. I was left with the hope that someone would hand it in and it would eventually make its way back to me. Incidentally, I think Track and Protect, with its owner information, reward and lock screen, significantly increases the chances of that happening.
However, it then occurred to me that I should try some of Track and Protect's other features to see if I could work out where the phone was. I sent off a command for a picture from the back camera, a completely dark image was returned, oh dear - it looked like it might be in some-one's pocket. I then sent a command from the front camera and was duly returned an image of a metal bar and various types of materials. I realised that this looked a lot like the underneath of a seat I had been sitting on earlier. A kind person went off check to the location for me, while I waited by the laptop (firing off more camera shot commands), and a short while later I was reunited with my E72 - result!

And it is true what they say, just like backups, you don't really appreciate an application like Track and Protect until the worst happens...
Conclusion
If your phone is lost or stolen then Track and Protect lets you lock it down so that your personal data is secure. It'll also prevent anyone running up expensive phone calls on the phone or gaining access to your social networks or similar services. More than that, it significantly improves the chances of you retrieving the phone.
If you lose your phone, as I did, I would suggest there's an excellent chance of retrieving it with the information and security lock enabled by Track and Protect. And if your phone is stolen then the potential level of information provided by Track and Protect (locations, alien SIM numbers, and pictures) is going to be very useful when talking to the police or other authorities. The more information you can provide, the more likely they will be able to help you.
Given the value of devices themselves, and the content stored on them, I would expect a service like Track and Protect to become increasingly popular. Indeed, manufacturers would do well to consider including this kind of functionality out of the box.
Having had a £300 phone 'saved' by Track and Protect means that I may be a bit biased in my positive attitude towards Track and Protect. But isn't that really the best accolade I can give it? When it came to the crunch, Track and Protect did the job it was designed to do. More than that, it was the extra functionality, the picture-taking ability, that really saved the day for me.
As such, and given the price point, I have no hesitation in recommending Track and Protect as an essential download for every Symbian smartphone owner.
Rafe Blandford, All About Symbian, July 20th 2010
You can download Track and Protect here (affiliate link). It is available for both recent S60 3rd Edition devices and all S60 5th Edition devices,
Reviewed by Rafe Blandford at
